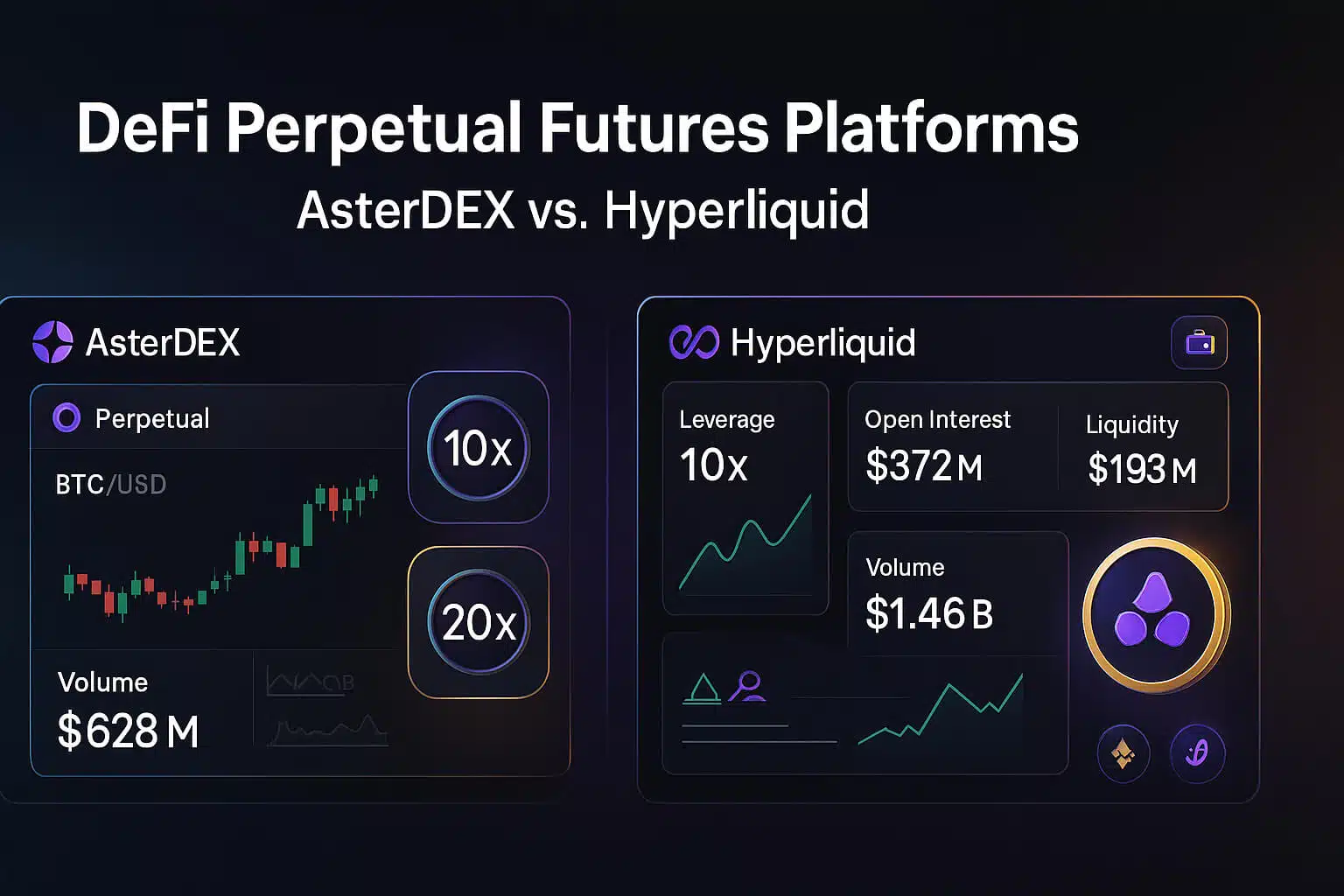
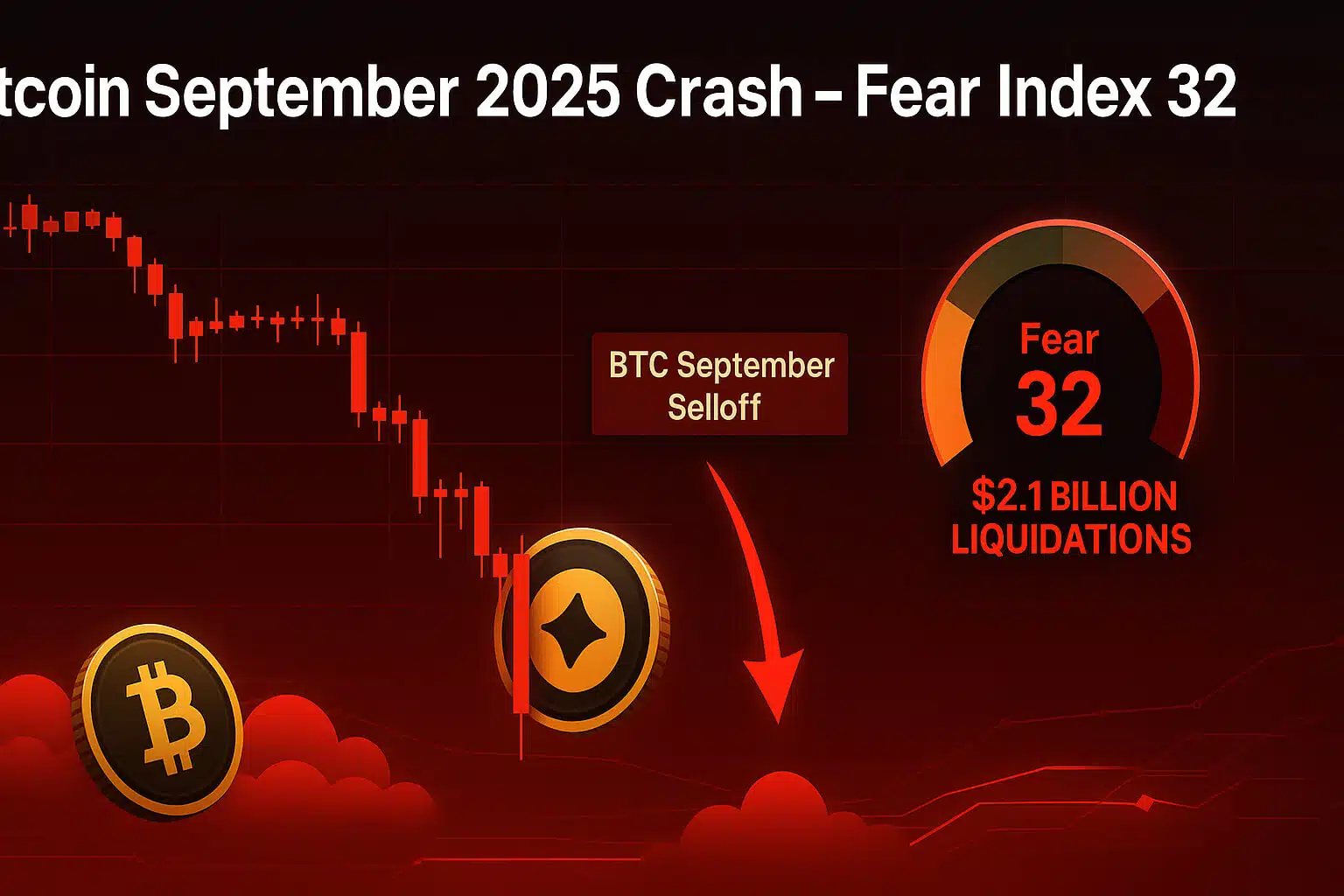
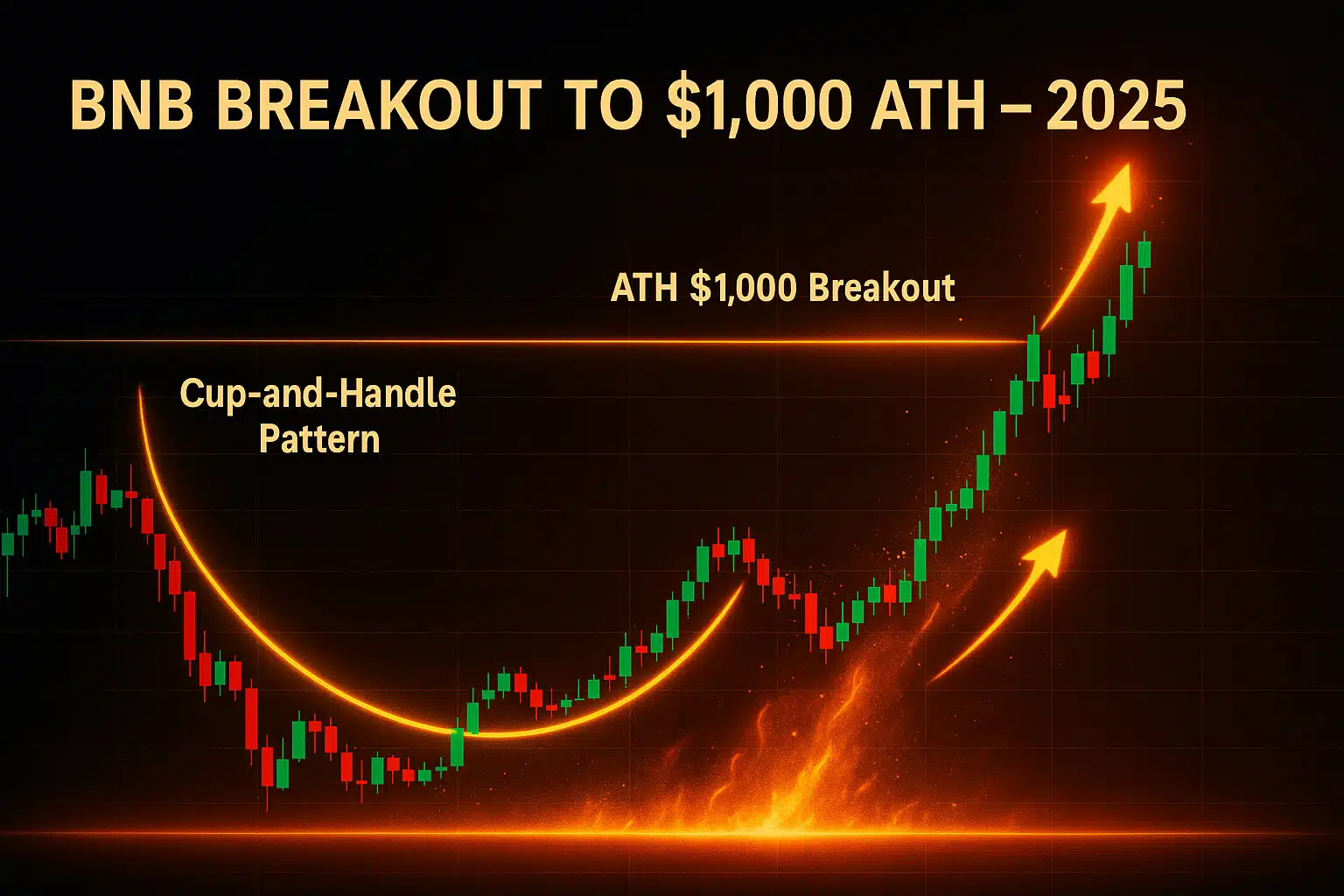
1. Introduction: The Evolving Landscape of Data Security
In today’s digital era, data has become a highly valuable asset, not just for businesses but also for individuals. However, as data becomes more critical, it also becomes more vulnerable to attacks, breaches, and unauthorized access. Traditional centralized storage systems, where data is stored on a single server or data center, show increasing limitations, particularly in terms of security and reliability. Decentralized storage solutions are emerging as a revolutionary alternative, offering enhanced data security through distributed networks and blockchain technology. This article explores how decentralized storage solutions are changing the landscape of data security, providing better protection and resilience.
Why Decentralized Storage Matters
The centralized nature of traditional storage systems leaves them susceptible to various security risks, including hacking, data breaches, and single points of failure. Decentralized storage distributes data across multiple nodes in a network, significantly reducing these risks and offering a more secure and reliable storage solution.
2. What is Decentralized Storage?
Decentralized storage refers to a method of storing data across a distributed network of computers or nodes, rather than relying on a single centralized server or data center. This approach contrasts with traditional cloud storage systems, where data is typically managed and controlled by a single entity, such as Google, Amazon, or Microsoft. In decentralized storage, data fragments are encrypted and distributed across multiple nodes, ensuring that no single node holds the entire dataset.
- Key Characteristics of Decentralized Storage:
- Distributed Network: Data is stored across a network of nodes, reducing the risk of a single point of failure.
- Redundancy: Multiple copies of data fragments are stored across the network, ensuring data availability even if some nodes go offline.
- Encryption: Data is encrypted before being distributed, adding an additional layer of security.
- Blockchain Integration: Many decentralized storage solutions use blockchain technology to manage data integrity and ensure transparency.
3. How Decentralized Storage Enhances Data Security
Decentralized storage offers several key advantages over traditional centralized storage systems, particularly in the realm of data security. Here’s how decentralized storage solutions are transforming data protection:
3.1 Elimination of Single Points of Failure
One of the primary security advantages of decentralized storage is its ability to eliminate single points of failure. In centralized systems, compromising a server puts all data stored on that server at risk. Decentralized storage, however, distributes data across multiple nodes, making it much harder for attackers to compromise the entire system.
- Example:
- In a decentralized network, even if one node is breached, the attacker only gains access to a fragment of the data, which is useless without the other fragments stored on different nodes.
3.2 Enhanced Privacy and Control

Decentralized storage gives data owners greater control over their information. Users can encrypt their data before storing it on the network, ensuring that only those with the decryption key can access the information. This level of control is particularly important in an age where privacy concerns are increasingly paramount.
- Example:
- Users can store sensitive information, such as personal documents or financial data, on a decentralized network with confidence that their data remains protected from unauthorized access.
3.3 Resistance to Censorship
Centralized systems can easily censor or remove data by the entity that controls the server. In contrast, decentralized storage operates without a central authority, making it much more difficult to censor or tamper with data. This resistance to censorship is one of the key benefits of decentralized networks.
- Example:
- Journalists or activists in restrictive regimes can store important information on decentralized networks, ensuring that their work remains accessible even if attempts are made to censor it.
3.4 Improved Data Integrity and Reliability
Blockchain technology, often used in decentralized storage solutions, ensures data integrity by maintaining an immutable record of all transactions and changes. This immutability makes it easy to detect tampering and verify the authenticity of data.
- Example:
- A blockchain-based decentralized storage system provides a verifiable audit trail for data, ensuring that any changes to the data are transparent and traceable.
4. Popular Decentralized Storage Platforms
Several decentralized storage platforms are leading the way in providing secure, distributed storage solutions. Here are some of the most prominent platforms:
4.1 Filecoin
Filecoin is one of the most well-known decentralized storage networks, developed by Protocol Labs. It allows users to rent out spare storage space on their computers in exchange for Filecoin tokens. The network stores data across a global peer-to-peer system, ensuring secure and distributed data storage.
- Key Features:
- Incentive-based storage model using Filecoin tokens.
- Redundancy and encryption to enhance data security.
- Blockchain-based auditing for data integrity.
4.2 Storj
Storj offers decentralized cloud storage by sharding data into smaller pieces and distributing it across a global network of nodes. It encrypts all data end-to-end, ensuring that only the data owner can access the full information. Storj’s decentralized architecture provides greater resilience and reliability compared to centralized cloud providers.
- Key Features:
- Sharding and encryption for high data protection.
- Redundant data storage across a distributed network.
- Transparent pricing with the STORJ token used for transactions.
4.3 Sia
Sia is a decentralized cloud storage platform where users can rent storage space from peers. Sia splits data into pieces, encrypts it, and distributes it across its network, ensuring that no single party controls the entire dataset. This decentralized approach enhances both privacy and security.
- Key Features:
- Data Privacy: Users maintain control over their encryption keys, ensuring that only they can access their stored data.
- Cost-Effective Storage: Sia offers competitive pricing compared to traditional cloud storage, with payments made in its native Siacoin (SC) token.
- Decentralized Control: Sia’s network distributes data across many nodes, making it resilient to censorship and attacks.
4.4 Arweave
Arweave is another decentralized storage platform that focuses on permanent data storage. It uses a unique consensus mechanism called Proof of Access (PoA) to incentivize nodes to store data permanently. Arweave’s blockchain-based storage system ensures that data remains accessible and unalterable indefinitely.
- Key Features:
- Permanent Storage: Arweave offers a unique “pay once, store forever” model, ensuring data is stored permanently on its network.
- Proof of Access: This consensus mechanism ensures that nodes continuously store and prove access to the data, keeping it available and secure.
- Decentralized Data Archive: Arweave’s network is designed to serve as a permanent, decentralized archive for important data, making it ideal for long-term storage needs.
5. Challenges of Decentralized Storage
While decentralized storage offers significant security advantages, it also comes with its own set of challenges:
5.1 Adoption and Integration
Adopting decentralized storage remains one of its biggest challenges. Businesses and individuals are often hesitant to move away from traditional, centralized solutions due to familiarity and established infrastructure. Integrating decentralized storage with existing systems can also require significant effort and technical expertise.
5.2 Performance and Speed
Decentralized storage networks can sometimes experience slower data retrieval speeds compared to centralized systems, especially if the network is not well-established or if data is stored on nodes with limited bandwidth.
5.3 Regulatory and Compliance Issues
The decentralized nature of these storage solutions can raise regulatory and compliance challenges, particularly in industries that require strict data governance. Ensuring that decentralized storage networks comply with data protection regulations like GDPR can be complex.
Conclusion: The Future of Data Security with Decentralized Storage
Decentralized storage solutions represent a significant step forward in the quest for more secure and resilient data storage. By eliminating single points of failure, enhancing privacy, and leveraging blockchain technology, decentralized storage provides a compelling alternative to traditional systems. However, challenges related to adoption, performance, and regulation must be addressed as the technology continues to evolve. As more businesses and individuals recognize the benefits of decentralized storage, it is likely to become a key component of future data security strategies.
For more insights and detailed guides on blockchain and decentralized technologies, explore our Blockchain Technology Guides section.
Stay Updated
For the latest updates on decentralized storage and data security trends, follow us on:
Stay informed with the latest strategies and insights in the world of blockchain and decentralized technologies at FreeCoins24.io.
Special Offer
Ready to explore decentralized storage solutions? Sign up on Bybit today and take advantage of up to $30,000 in deposit bonuses. Start your journey with a trusted platform.